Dec 6, 2024
Code review is an essential practice in modern software development, aimed at inspecting source code for potential problems, such as bugs, vulnerabilities, and compliance with coding standards. Code reviews play a crucial role in the software development lifecycle, helping to maintain code quality and reliability. Traditionally, developers have conducted code reviews manually, examining each other's code to spot potential problems.
However, with advancements in automation and artificial intelligence, code reviews can now be automated using specialized tools. In this blog, we’ll explore the advantages of automated code security reviews and why integrating them into your development workflow can be highly beneficial.
What is an Automated Code Review Process and How Does it Work?
Automated code review leverages software tools to analyze and assess code for vulnerabilities, bugs, and compliance with coding standards. These tools streamline the review process, minimize human error, and facilitate quicker, more reliable software development. They assist developers by efficiently scanning extensive codebases to uncover security flaws, performance issues, and suggest best practices. By catching problems early in the development cycle, these solutions enhance code quality, security, and maintainability.
The process uses software to check code against a set of predefined guidelines, offering a faster and more thorough analysis. These tools look for security risks, style inconsistencies, errors, and inefficient practices. When anomalies are detected, developers can use the feedback to update their codebase. Additionally, these tools can integrate with code management platforms like GitHub, providing real-time alerts when issues arise during the review.
Importance of Automated Code Security Review
Imagine a scenario where your team has put in tremendous effort to develop a new software product. You’re confident that most major issues have been addressed before launch. So, why consider running an automated code review, right? The answer lies in the potential consequences.
In 2024, the average cost of a data breach reached $4.88 million, a figure that continues to rise. However, companies leveraging automated security measures managed to save an average of $2.22 million.
Beyond the direct financial impact, a security breach can lead to serious long-term damage. This includes loss of customer trust, harm to reputation, and potential legal consequences — challenges no business can afford to ignore.
Automated code security review involves using software tools to automatically inspect source code for issues like bugs, security risks, and breaches of coding standards. These tools are intended to support human reviewers by highlighting potential problems that may need further investigation. Typically, they are executed via pre-commit hooks or integrated into CI/CD pipelines, providing almost real-time feedback throughout development.
Next, we discuss the difference between code linters and automated code security suites.
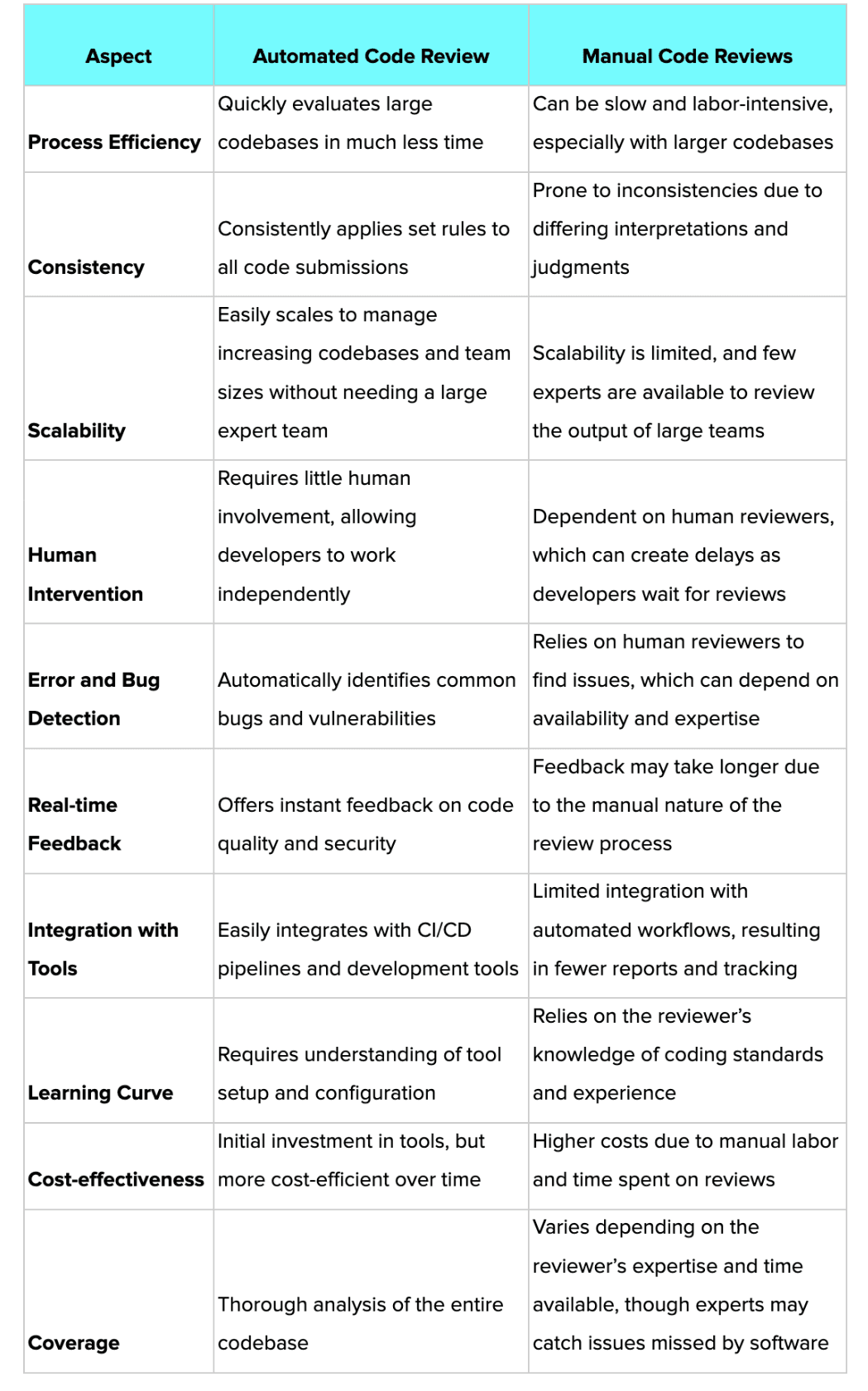
Automated Code Review vs Manual Code Review
Automated and manual code reviews each offer distinct advantages. Here are some benefits of automated code reviews:
Faster Error Detection
Automated tools can rapidly analyze extensive codebases, identifying errors, bugs, and security vulnerabilities more efficiently than human reviewers.
Reduced Human Oversight
By adhering to established rules and guidelines, automated tools provide consistent and comprehensive reviews, minimizing the risk of mistakes due to human oversight.
Elimination of Bias
Automated tools perform objective reviews based on set standards, reducing the impact of personal preferences or unconscious biases that may influence manual reviews.
However, automated code reviews come with certain limitations, such as:
Contextual Understanding
Automated tools may miss the broader context or the intent of specific code sections, potentially leading to false positives or failing to catch subtle issues.
Limited Analysis Scope
These tools primarily address syntax, style, and known patterns, whereas human reviewers can evaluate broader aspects like architectural and design considerations.
Inflexibility
Although machine learning is advancing, automated tools still lack the adaptability of human reviewers, who can understand and apply knowledge of new technologies and evolving coding practices.
Here’s the key differences between manual code reviews and automated code reviews.
What are the key capabilities that you must eye for in an automated code security review process? We will discuss it next!
5 Key Capabilities to Look For in Automated Code Review Tools
When selecting an automated code review tool, it’s essential to evaluate the following key features and capabilities.
1. Collaboration
A tool that facilitates collaboration is critical for enhancing communication, knowledge sharing, and teamwork among developers. Since team members bring diverse skills and perspectives, a collaborative environment fosters idea exchange and collective problem-solving, ultimately improving the quality of the codebase. Tools that promote collaboration help manage differing opinions constructively during the review process, ensuring the best solutions are implemented. By working together, developers can identify and resolve issues more efficiently, while also learning from one another’s experiences, leading to continuous improvement.
2. Security
Employing a secure static code analysis tool is crucial for safeguarding software security, quality, and reliability. These tools examine the source code without executing it, detecting vulnerabilities, coding standard violations, and other issues that could compromise the software. By identifying security flaws early in development, teams can address problems before they become critical in production, reducing remediation costs. Static analysis tools also enforce consistent coding practices, resulting in cleaner, more secure code, and provide feedback on security best practices, helping developers enhance their coding skills.
Additionally, some static analysis tools use behavioral analysis to understand the code's intended behavior, flagging potential threats that may not be detected through standard syntax checks. This adds another layer of security, making the software more resistant to attacks and exploitation.
3. Integrations
A code review tool with strong integrations is essential for optimizing workflows and improving efficiency. Whether web-based or self-hosted, the tool should adapt to various project needs and existing toolchains, allowing for flexibility and customization. Seamless integration with popular repositories, such as Git, ensures smooth management of version control, tracking changes, and handling branching or merging operations without interrupting the development process.
It’s also beneficial for the tool to integrate with deployment tools and CI/CD pipelines, providing real-time feedback. This allows developers to catch issues early in the development cycle, reducing the risk of deploying faulty code.
4. Metrics and Analytics
A customizable code review tool is valuable for addressing different project needs and team preferences. It should offer the ability to track and report metrics that are most relevant to a project, ensuring a targeted approach to improving code quality. Additionally, the tool should support a variety of programming languages, frameworks, and libraries, making it suitable for a wide range of teams and projects.
5. Visualization
Visualization capabilities in a code review tool enhance understanding, improve efficiency, and streamline communication during the review process. Visual representations of the code, such as UML diagrams, flowcharts, and code maps, allow reviewers to quickly grasp relationships between different parts of the code. This helps focus attention on critical areas, facilitating quicker identification of issues and more effective feedback.
Read More: Types of Application Security Testing Tools
Next, we discuss how automated code security reviews reduce false positives.
Reducing False Positives & False Negatives
Since no automated code checker is flawless, there is always a chance of encountering false positives or false negatives during a code review. Here’s a breakdown of these terms:
False Positive: Occurs when the analyzer flags an issue where no rule has actually been violated. While not harmful in itself, this increases the time developers spend distinguishing between actual errors and incorrect alerts. True positives are legitimate issues that require attention, whereas false positives divert a developer's focus unnecessarily.
False Negative: Happens when the analyzer fails to detect a real issue, allowing it to pass unnoticed during the review. This undetected problem represents a significant risk that an effective automated code review system aims to prevent.
How Automated Code Security Review Reduces False Positives?
Automated Code Security Review can significantly reduce false positives through various methodologies and technologies designed to enhance accuracy in identifying genuine vulnerabilities. Here are the key strategies:
1. Proof-Based Scanning
Proof-Based Scanning is a technique that automatically verifies whether a suspected vulnerability can be exploited. By attempting to exploit the vulnerability, the tool provides definitive proof of its existence, thus minimizing false positives. This method allows developers to focus on verified vulnerabilities rather than sorting through numerous suspected issues, which can lead to quicker resolutions and improved productivity.
2. Advanced Scanning Tools
Utilizing high-quality, robust automated scanning tools is crucial. These tools often incorporate extensive databases of known vulnerabilities and employ sophisticated algorithms to differentiate between true vulnerabilities and false positives. For instance, tools that integrate artificial intelligence can analyze code more effectively, reducing the likelihood of misidentifying benign code as problematic.
3. Contextual Awareness
Context is vital in reducing false positives. Automated tools that understand the specific context of an application—such as its data flow and input validation mechanisms—are less likely to flag non-issues. This means that tools should be configured to consider the unique characteristics of the code being reviewed, which can help in accurately assessing security risks.
4. Simplified Code Logic
Developers can reduce the complexity of their code logic, making it easier for automated tools to identify potential vulnerabilities accurately. Simplifying code flow by minimizing nested structures or excessive conditional statements can reduce the number of false positives.
5. Continuous Learning Mechanisms
Implementing systems that learn from previous scans can also help in reducing false positives over time. For example, when a team identifies a false positive, they should be able to report it back into the system, which then updates its algorithms accordingly. This feedback loop allows for continuous improvement in detection accuracy.
6. Integration with Development Processes
Integrating automated security reviews into the development lifecycle ensures that security checks occur regularly and efficiently. When developers receive actionable insights directly into their issue tracking systems without needing manual verification of scan results, it streamlines the process and reduces the chances of overlooking real vulnerabilities amidst false alarms.
Benefits of Reducing False Negatives in Automated Code Reviews
Reducing false negatives in automated code reviews is crucial for enhancing software quality and security. Here are the primary benefits:
Improved Code Quality
Lowering the occurrence of false negatives ensures that genuine issues are not overlooked, leading to higher overall code quality. This means that potential bugs, security vulnerabilities, and other defects are more likely to be identified and addressed before the code reaches production.
Enhanced Security Posture
By minimizing false negatives, organizations can better detect security vulnerabilities that could be exploited by attackers. Automated tools that accurately identify these issues help protect sensitive data and maintain user trust, as they reduce the chances of security breaches.
Increased Developer Confidence
When developers know that their automated code review tools are effective at catching real issues, they can trust the feedback provided. This confidence encourages them to rely on automated processes, leading to a more efficient workflow and reduced manual review fatigue.
Faster Time-to-Market
By ensuring that fewer critical issues go undetected, teams can resolve problems earlier in the development cycle. This proactive approach accelerates the development process and allows for quicker releases, giving organizations a competitive edge in fast-paced markets.
Cost Efficiency
Addressing issues early in the development process is typically less expensive than fixing them after deployment. By reducing false negatives, organizations can avoid costly post-release fixes and minimize disruptions in their development cycles.
Why Using Automated Code Reviews is the Right Approach?
Manual code reviews are essential in software development. They bring in multiple expert viewpoints to catch logic errors, ensure the code functions as intended, and hold developers accountable, knowing their work will be scrutinized.
However, while manual reviews are effective at evaluating logic and purpose, incorporating an advanced automated code review can significantly speed up the process and enhance application security and efficiency. Automated reviews identify more issues faster, boosting both the speed and precision of the development workflow.
Read More: A Guide To Current Threat Modeling Practices In SDLC
Next, we discuss how security focused automated code review tools are balancing the cybersecurity efforts.
5 Security-focused Automated Code Review Tools
Here are the best 5 security focused automated code review tools.
Snyk
Snyk is an automated code review tool designed to detect security vulnerabilities in open-source libraries and packages. Unlike traditional analysis tools that focus on your custom code, Snyk identifies risks in the libraries and external code dependencies you use.CodeQL
CodeQL, developed by GitHub, is a robust static analysis tool used to discover security vulnerabilities and bugs. It analyzes a program's source code and constructs a database that helps identify how the code behaves, making it easier to spot potential issues.Checkmarx
Checkmarx is a commercial application security tool that performs data flow analysis to detect vulnerabilities across various programming languages like Java, .NET, C++, Python, and PHP. It uses a proprietary engine to identify issues such as SQL injection, cross-site scripting (XSS), and buffer overflow vulnerabilities.CodeSonar
CodeSonar is a commercial analysis tool that uses data flow techniques to detect problems in languages like C, C++, Java, Kotlin, JavaScript, and Python. It can evaluate both source code and binaries, identifying issues such as buffer overflows, null pointer dereferences, and use-after-free errors. It provides comprehensive static application security testing (SAST).Coverity
Coverity was initially a large-scale research collaboration with the U.S. Department of Homeland Security aimed at enhancing the security of open-source software. Now managed by Synopsys, it continues to offer a free service to open-source projects while providing a paid solution for broader software security needs.
Read More: Top 7 Automated Threat Modeling Tools - A Comparison In 2024
Conclusion
Having an expert team review new code for its logic and intent is immensely valuable. However, combining this manual process with automated code security review can help identify publicly known vulnerabilities, as well as those introduced through custom code and potential security risks. Thus, conducting an automated code review becomes an essential step while developing a high-quality, secure application.
What if there was a platform that leverages Gen AI to scale security design reviews? Seezo.io streamlines threat modeling using GenAI. Seezo accepts documentation such as JIRA tickets, Google documents and architecture diagrams to come up with threats and associated security requirements to avoid the threats being introduced. Additionally, it helps come up with priority buckets for the features that are being built.
Initiate automated security design reviews with Seezo.io to ensure protection right from the first line of code. Request a demo now!

