Oct 18, 2024
Introduction
In today’s software development environment, developers strive to release code quickly while maintaining application security. However, the software supply chain involves a complex network of individuals, processes, and tools, making it difficult for developers to catch every possible vulnerability on their own. This is where Static Application Security Testing (SAST) proves its mettle.
One of the most effective ways to ensure security from the very beginning of the development process is through static application security testing (SAST). SAST tools are a vital part of any organization's security strategy, as they help developers detect vulnerabilities early in the software development lifecycle (SDLC). This blog will explore SAST in depth, focusing on its importance, how it works, and best practices for integrating it into your development processes.
What is Static Application Security Testing (SAST)
Static Application Security Testing (SAST) refers to a method of security testing that examines the source code or binaries of an application without executing the program. By analyzing the static code at rest, SAST identifies vulnerabilities related to coding errors, weak security practices, and potential threats like buffer overflows, injection flaws, and improper input validation.
The purpose of SAST is to provide developers with insights into security flaws before the code reaches production, allowing them to resolve issues early and avoid costly post-release fixes.
Early Implementation of SAST
SAST tools provide the maximum value when implemented early in the SDLC. When vulnerabilities are detected early, they can be corrected with minimal effort, reducing both the cost and complexity of fixing issues. By identifying vulnerabilities in the initial phases of development, SAST helps reduce the chances of these issues being exploited in production environments.
Advantages of early SAST implementation:
Reduces costs of fixing vulnerabilities.
Minimizes delays in the development process.
Reduces the risk of deploying insecure applications.
Increases overall software quality and security.
SAST in Software Development Lifecycle
Security is a shared responsibility, and it should be embedded into every stage of the SDLC. SAST helps integrate security into development by identifying vulnerabilities before deployment. In industries like fintech and healthcare, where sensitive information is handled, ensuring security from the start is critical. By incorporating static application security testing as part of the SDLC, you can ensure that your applications meet security standards before they reach production.
Understanding How SAST Works
Static Application Security Testing (SAST) is a powerful tool in the software development process, designed to identify vulnerabilities early by scanning code before it's executed. This methodical approach ensures potential security flaws, logic errors, and insecure coding patterns are flagged during the development phase, enabling developers to address issues before they become critical. In this section, we’ll explore the mechanics behind SAST, from scanning static in-house code to leveraging rule-based analysis for effective vulnerability detection.
1. Scanning Static In-House Code at Rest
SAST tools operate by scanning the application's source code, bytecode, or binaries without running the application. This method analyzes the structure and logic of the code, seeking out vulnerabilities and coding flaws. Since SAST doesn't require the code to be running, it can be integrated directly into the development phase, allowing developers to address issues early.
2. Core Mechanics
SAST tools work by systematically examining the code to identify weaknesses. They look for insecure coding patterns and vulnerabilities based on predefined rules or guidelines. These tools typically support a range of programming languages and are capable of analyzing large codebases efficiently.
3. Processes: Lexical Analysis, Syntax Analysis, Control Flow, and Data Flow Analysis
Lexical Analysis: This process breaks down the code into tokens, which represent small parts of the code like keywords, operators, and identifiers.
Syntax Analysis: The tool checks whether the code complies with the grammar of the programming language being used.
Control Flow Analysis: This analyzes the paths that data can take through the code, helping identify potential logic errors.
Data Flow Analysis: This process tracks the movement of data within the program to uncover security issues related to how data is accessed and modified.
Together, these processes help SAST tools detect vulnerabilities before the code is executed.
4. Pattern Matching and Rule-Based Analysis
SAST tools employ pattern matching to identify common security vulnerabilities like injection attacks, buffer overflows, and improper error handling. Using predefined security rules, SAST can compare the code with a set of known vulnerabilities to flag potential risks. Rule-based analysis allows for highly targeted assessments of coding practices.
Challenges of Static Application Security Testing
While Static Application Security Testing (SAST) offers significant advantages, it also presents several challenges. Key difficulties include:
False Positives and Negatives: SAST tools can produce false positives (flagging non-existent issues) or false negatives (missing actual vulnerabilities), leading to unnecessary effort spent on investigating irrelevant problems or overlooking critical flaws.
Complex Code Analysis: Analyzing large, complex codebases—especially those involving multiple languages, frameworks, and libraries—can be difficult for SAST tools, potentially resulting in incomplete or inaccurate scans.
Integration with Development Workflows: Seamlessly integrating SAST into development processes without affecting productivity is challenging. Developers might view security testing as disruptive, leading to resistance or skipping security checks altogether.
Limited Detection: Certain vulnerabilities, such as configuration errors, design issues, or flaws in business logic, may not be detected by SAST tools, requiring the use of other testing methods for comprehensive coverage.
Resource-Intensive: Running SAST scans on large projects can be demanding in terms of time, computing power, and human effort, particularly when used regularly in CI/CD environments.
Skill Requirements: Properly configuring SAST tools and interpreting their results requires specialized knowledge, which may not always be present within development teams.
Integrating SAST into the Development Process
Here is how you can integrate SAST into a development environment smoothly.
Step 1: Building the Foundation
The first step in integrating SAST is thoroughly assessing your current development environment to identify where SAST can be most effectively applied. Choose a SAST tool that integrates well with your team’s languages and frameworks while being easy to use for smoother adoption. Training your team to incorporate SAST into their daily routines is essential for successful integration, ensuring everyone understands its importance in the development process.
Step 2: Integrating SAST in the Development Phase
Integrating SAST early in development is crucial for maximizing its effectiveness. By making SAST a core part of your process, your team can quickly identify and fix vulnerabilities before they reach production. This proactive approach prioritizes security from the start. Additionally, implementing continuous scanning ensures ongoing monitoring of your codebase, allowing real-time detection of emerging issues. This not only strengthens your product's security but also fosters a security-conscious mindset within your development team, embedding security into the entire development lifecycle.
Step 3: Incorporating SAST into Code Review and CI/CD Pipelines
In this phase, SAST becomes integral to your code review process, adding a crucial layer of security. By integrating SAST into your CI/CD pipelines, you automate security checks, embedding them into every development and deployment stage. SAST insights in Pull and Merge Requests turn code reviews into collaborative sessions focused on strengthening security. All these ensure that every line of code undergoes thorough scrutiny, with vulnerabilities identified and resolved before reaching the main branch.
Step 4: Prioritizing Findings
Effectively managing SAST findings starts with a clear prioritization strategy. Critical vulnerabilities should be addressed first without overlooking less severe issues. This process is not just about fixing security flaws—it's an opportunity to build a collaborative security mindset within your team. Encourage developers to work together to address these findings, fostering a shared commitment to security throughout the development process.
Step 5: Regular Audits and SAST Updates
Ensuring the security of your codebase requires consistent and thorough audits. Regularly scheduled full scans are vital for detecting and addressing critical vulnerabilities before they reach production. This proactive approach helps maintain strong security defenses for your application, providing ongoing protection against potential threats.
SAST vs. Other Security Testing Methods
When it comes to ensuring software security, various testing methods like Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Software Composition Analysis (SCA) are widely used. Understanding the differences between them is crucial to employing the right tools at the right stages of development. Below, we’ll explore how SAST compares to DAST and SCA, as well as how combining these tools can provide a comprehensive security assessment.
1. SAST vs. DAST
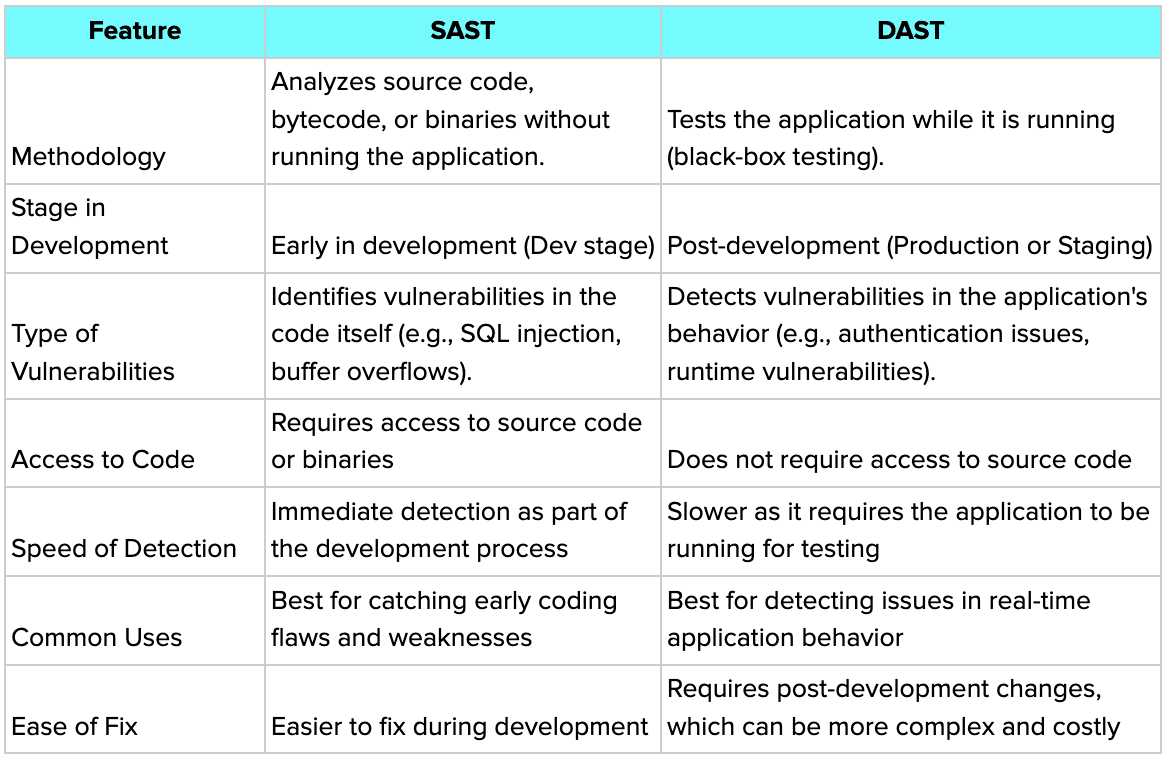
Key Differences:
SAST scans for vulnerabilities in code that is not running, allowing developers to find and fix issues during development.
DAST, on the other hand, simulates real-world attacks on a running application to find vulnerabilities that manifest during execution.
2. SAST vs. SCA
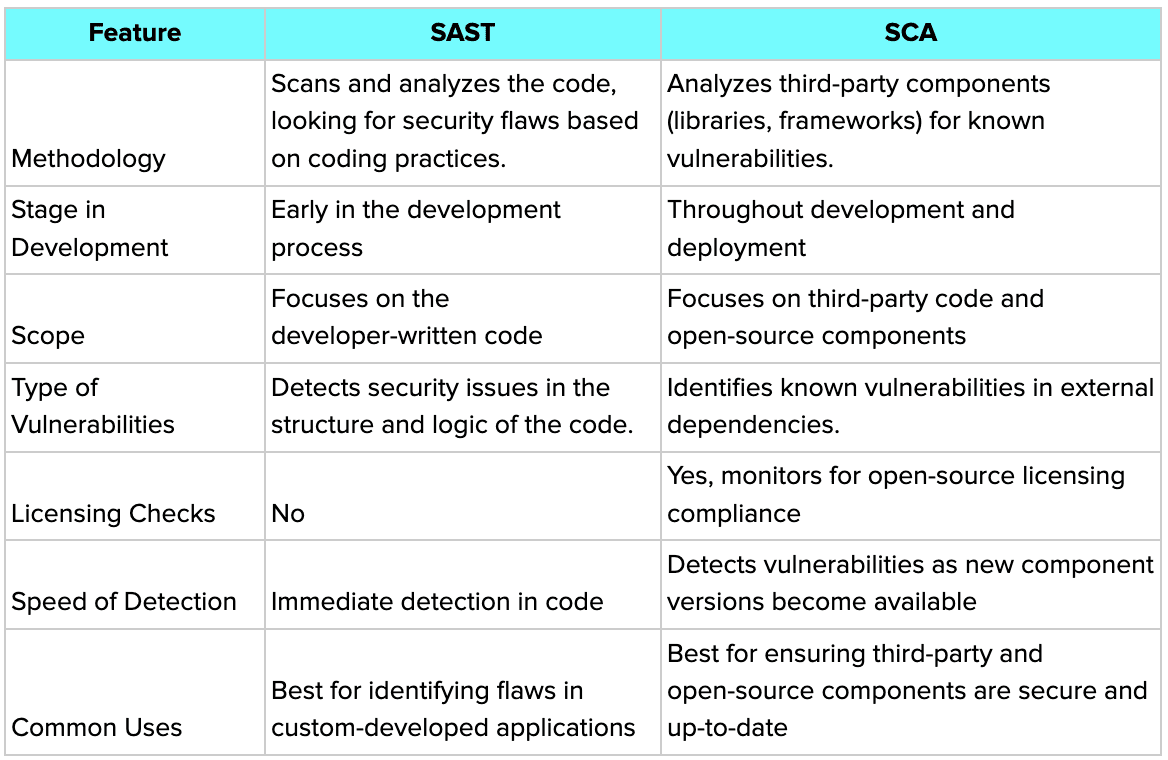
Key Differences:
SAST targets security weaknesses in your custom code, while SCA ensures the external libraries and dependencies you rely on are safe and compliant with licensing.
3. Combining SAST, DAST, and SCA for a Comprehensive Assessment
Each of these tools excels in different areas of security testing, but to achieve the most comprehensive protection, they should be used together. Here’s how combining these methods offers better security:
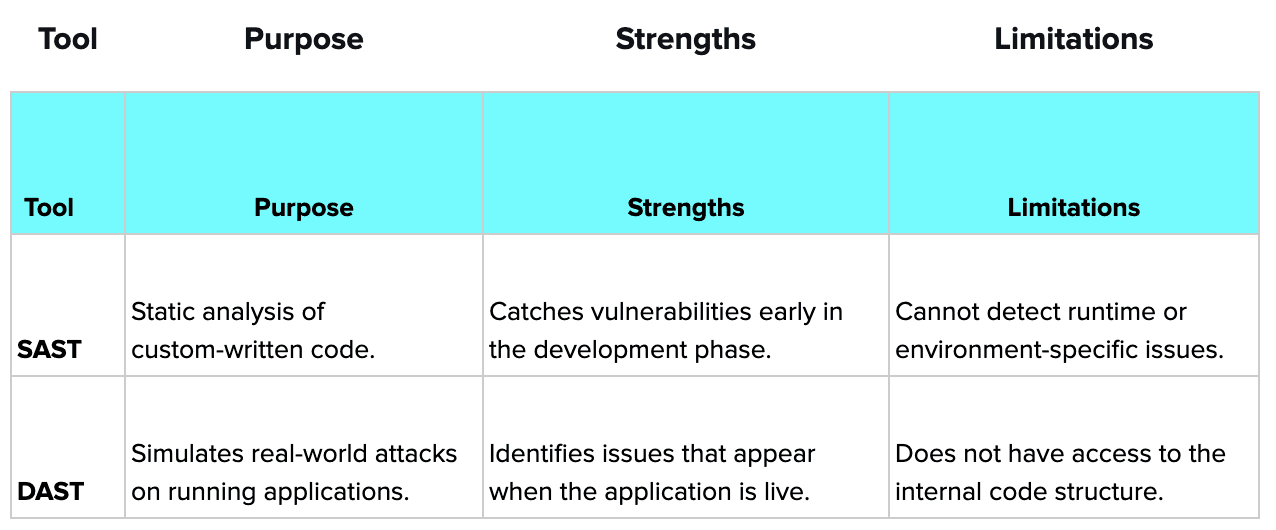
Benefits of Combining:
Comprehensive Coverage: By combining SAST (static analysis), DAST (runtime testing), and SCA (third-party component analysis), you cover all aspects of security, from coding practices to external dependencies and runtime behavior.
All-Stage Detection: SAST can be used in early stages of development to catch coding flaws, while DAST provides insights into vulnerabilities that only emerge during runtime. SCA continuously ensures third-party libraries are safe.
Choosing the Right SAST Tool
Selecting the right Static Application Security Testing (SAST) tool can be challenging for developers and security teams. This section will guide you through the key factors to consider before making your decision.
1. Accurate Vulnerability Detection
The main objective of a SAST tool is to find vulnerabilities in the code. A reliable SAST solution should have the capability to accurately detect and identify both common and complex vulnerabilities. It should also have an extensive database of known security issues to ensure comprehensive detection.
2. Performance
When choosing a SAST tool, performance is crucial. It must be fast and efficient, ensuring that the development process is not slowed down. For larger projects with extensive code, the tool should be able to analyze quickly and deliver timely results, allowing development to continue smoothly.
3. Holistic Application Awareness
Holistic Application Awareness refers to the tool’s ability to assess the overall security of an application. It should not only analyze individual code snippets but also understand how different parts of the code interact. Look for SAST solutions that can assess the security posture comprehensively, including static analysis, secrets detection, and Infrastructure as Code (IAC) analysis.
4. Integration with Development Tools
Integrating with development tools is a crucial aspect of SAST solutions. Developers should be able to embed the tool within the development workflow, where it functions harmoniously with the existing tools they utilize. An effective SAST tool should seamlessly connect with platforms like GitHub, JIRA, and Slack. This integration allows developers to receive immediate notifications when vulnerabilities are identified, thereby facilitating a more efficient remediation process.
5. Actionable Insights (Reporting)
An effective SAST tool must deliver comprehensive and user-friendly reports. These reports should offer an in-depth overview of the vulnerabilities found within the organization's codebase. Additionally, they should include actionable remediation guidance for developers. The SAST tool should also provide key metrics that allow engineering managers to assess the effectiveness of their security initiatives. For instance, it should empower teams to identify and address violations related to the OWASP® Top 10 and SANS/CWE Top 25 in both new pull requests and existing code.
Conclusion
Selecting the right SAST tool involves considering factors like vulnerability detection accuracy, performance, holistic application awareness, and seamless integration with development tools.
By adopting SAST and integrating it into your development workflow, your organization can enhance the security, reliability, and quality of your software while minimizing costly post-release fixes.
But that’s just the beginning! By combining SAST with other security testing methods—like Dynamic Application Security Testing (DAST) and Software Composition Analysis (SCA)—you can create a comprehensive security strategy that covers every aspect of your development lifecycle.
Enter Seezo.io - a revolutionary platform designed for automated security design reviews. With Seezo.io, you can deliver tailored security requirements to your developers early in the development cycle, ensuring that security is woven into the fabric of your process from day one.
Book a demo today to discover how Seezo.io can assist in identifying and addressing vulnerabilities before they become risks.

