Dec 6, 2024
Security is a critical aspect of any application with essential functionality. It can range from protecting your database against malicious attacks to handling fraud detection on leads before adding them to your platform. Security should be integrated into every stage of SDLC to create a Secure Software Development Lifecycle (SSDLC). This ensures that security is proactively managed from requirements gathering to deployment, reducing the risk of vulnerabilities at each stage.
By practicing the best SSDLC approaches and using effective security solutions, potential vulnerabilities can be identified early in the process, well before production. This approach not only reduces the chances of security flaws in your app but also helps limit the damage if any are discovered. In this article, we’ll discuss how to build a secure software development lifecycle (SDLC), ensuring issues are caught early in the requirements phase, preventing them from becoming security risks in production.
What is Secure SDLC or SSDLC?
Secure Software Development Life Cycle (Secure SDLC or SSDLC) is an approach that integrates security practices into each phase of the traditional Software Development Life Cycle. Rather than treating security as a final step before deployment, SSDLC emphasizes building security measures throughout the entire development process. This proactive approach ensures that vulnerabilities are identified and mitigated early, reducing the risk of costly fixes and security breaches after release.
The SSDLC process typically starts with security requirements and threat modeling during the planning and analysis phases. During design and development, secure coding standards and static code analysis are implemented to maintain code quality and minimize risks. In the testing phase, security testing techniques, such as penetration testing and dynamic analysis, are used to identify vulnerabilities. Finally, the deployment phase involves secure configuration and monitoring.
By embedding security from the start, SSDLC enhances the overall resilience of applications, ensures compliance with industry standards, and protects sensitive data from potential threats.
Here’s why secure SDLC is essential.
Why is Secure SDLC Essential?
Secure SDLC is vital because application security is crucial. The approach of launching a product and fixing bugs later with updates is no longer viable. Developers must now consider security risks at every phase of the process. This means embedding security into the SDLC in ways that weren’t necessary before.
With the possibility of unauthorized access to your source code, it's important to write code with potential vulnerabilities in mind. A strong, secure SDLC process is key to protecting your application from attacks by malicious users. Tools like application security posture management can offer a comprehensive view of your security framework and provide insight into any vulnerabilities.
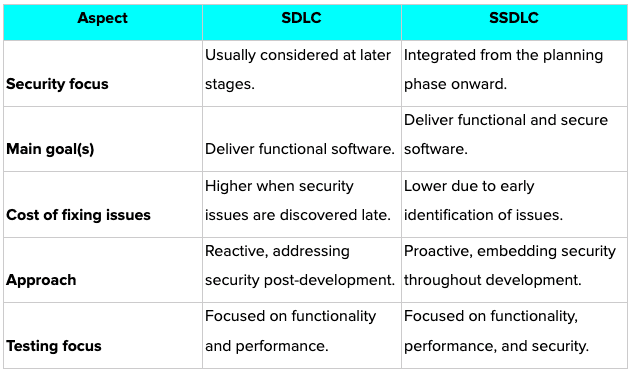
SSDLC vs. SDLC: What’s the Difference?
When implemented correctly, an SSDLC introduces several important elements that a standard SDLC typically lacks. The table below highlights the key distinctions between SSDLC and SDLC.
Next, we discuss the various phases of the secure SDLC.
How to Embed Security into All Phases of the SSDLC?
Integrating security into the software development lifecycle (SDLC) should be viewed as an ongoing process, woven throughout, rather than as a separate task. There isn’t a distinct "security phase"; instead, best practices and tools should be applied during each existing SDLC phase. By involving stakeholders in security, leveraging automated tools, and focusing on continuous education, security becomes a natural extension of the development process—making it both more sustainable and beneficial.
Listed below are the various phases involved in secure software development lifecycle (SSDLC).
Planning
After identifying the problem, the next step is determining the solution. This phase involves deciding what will be built. Input from the security team is crucial to ensure the proposed solution not only addresses the problem but also provides a secure outcome for the customer.
Seezo.io is a platform that specializes in providing automated security design reviews for software features. It aims to deliver context-specific security requirements to developers before they begin coding, ensuring that security considerations are integrated into the development process from the outset.
Requirement and Analysis
The initial phase defines the problem, establishes security needs, and clarifies what success looks like. Here, feature requests, bug reports, and vulnerability disclosures turn into actionable projects. The main challenge lies in prioritizing security. Including security experts during grooming helps to assess the security impact of each new feature entering the SDLC.
Example of a functional requirement: Users must have the capability to verify their contact details before renewing their membership.
Example of a security consideration: Users should have access only to their own contact information and not be able to view anyone else’s.
Design and Prototyping
Once the security requirements are established, it’s time to plan how the solution will be integrated into the application. This includes outlining the entire architecture, determining which systems and services will be affected, and understanding how users will interact with the feature. Just as engineering teams review designs for functionality, the security team should review them to catch any potential vulnerabilities.
A preliminary design is created, which serves as a blueprint for the prototype, providing a basic structure without going into exhaustive detail. This prototype includes key functionalities that allow users to interact with it and provide feedback. Users provide feedback on their experience, which informs further refinements. Based on user feedback, the prototype is revised and improved.
Development
Coding comes at this development phase, where security practices come into action. Using static analysis tools for every commit or push provides developers with immediate feedback about code quality and security. During code reviews, teams should actively look for both logical errors and security risks. Every team member plays a role in maintaining security, not just the security specialists.
However, today's application developers must consider more than just the code they create, as most modern applications are not entirely built from the ground up. Instead, developers frequently use existing functionalities, often from free open-source components, to add features and bring value to the organization efficiently. In fact, over 90% of modern applications consist of these open-source components, which are typically analyzed using Software Composition Analysis (SCA) tools.
Testing & Deployment
Once the code is written and reviewed, thorough testing begins. Advanced security scanning tools are used to perform in-depth analysis, and depending on the scope of the feature, manual security testing can also be conducted. When vulnerabilities are found, solutions can be integrated into automated tools to prevent future issues.
Testing during this phase can involve:
Automated tests to validate the critical paths of your application
Automated unit tests to ensure the correctness of the application's core functionality
Automated deployment tools that securely integrate application secrets for use in a production setting
Once the tests are done, the software is ready for deployment.
Maintenance
The release of an application doesn’t mark the end of its story. Vulnerabilities that were missed during development can be discovered long after the launch. These security flaws may exist in the developers’ code but are increasingly identified in the open-source components that make up the application. This has led to a rise in “zero-day” vulnerabilities, or previously unknown security issues detected in production by the app’s maintainers.
When these vulnerabilities are found, the development team must patch them, sometimes requiring extensive rewrites of key features. Additionally, vulnerabilities may be identified through other means, such as external penetration tests by ethical hackers or public submissions via “bug bounty” programs. Planning to address these production issues and incorporating them into future updates is essential.
Repeat
The secure SDLC operates as a cycle, not a linear path. Each bug, enhancement, or vulnerability discovered in the testing and maintenance phases will initiate a new requirements phase. Secure software development is an ongoing cycle of refinement and improvement.
Read More: Threat Modeling With Automated Penetration Testing: A Detailed Guide
Next, we discuss the best practices for secure SDLC.
Top 8 Best Practices for Secure SDLC
The best practices for secure sdlc are as follows:
Educate Your Developers
A secure SDLC involves several connected initiatives, such as developing secure coding guidelines, offering security awareness and coding training, and defining clear remediation SLAs for addressing production issues. While not all elements are required for effective implementation, you’ll need to assemble enough components to form a complete picture, similar to a puzzle.
Set Clear Requirements
Any security guidelines, advice, or requirements should be straightforward and actionable. Development teams need easy-to-understand instructions, and any identified vulnerabilities must come with clear solutions. The focus should be on offering actionable steps, not just pointing out issues.Encourage a Growth Mindset
Since SSDLC impacts how teams collaborate, it’s crucial for everyone to approach the process with an open mindset. The security team should aim to empower developers to take ownership of securing their applications.Align with Other Initiatives
For established teams or applications, integrating SSDLC changes can be smoother when tied to other modernization efforts like cloud transformation, DevOps, or DevSecOps initiatives.Address Critical Issues First
Prioritize fixing the most pressing security vulnerabilities. In large or older applications, addressing every issue may not be feasible, so a triage approach is useful—focusing on preventing new vulnerabilities and gradually resolving existing ones.Look to Established Secure SDLC Frameworks
Unsure about how to begin with secure SDLC? Explore well-known frameworks like OWASP's Comprehensive Lightweight Application Security Process (CLASP), NIST's Secure Software Development Framework (SSDF), etc. These frameworks offer valuable guidance and practical examples suited for various application types and development environments.
7. Proactively Ensure Security
Evaluate the deployment environment for vulnerabilities before launching software and apply controls to mitigate risks. Continuous monitoring for security threats enables quick detection and response. Regular security assessments of architecture, design, and deployment are essential.
8. Effectively Address Vulnerabilities
Use tools like static analysis and code reviews to identify vulnerabilities promptly. Prioritize responses based on impact, and communicate transparently with stakeholders about issues and corrective actions to build trust.
Read More: A Guide To Current Threat Modeling Practices In SDLC
Next, we discuss the advantages of secure SDLC.
What are the Benefits of Secure SDLC?
Incorporating security into every stage of the Software Development Lifecycle offers numerous advantages. SSDLC makes security a shared responsibility and ensures software is developed with security in mind from the beginning. The key benefits are as follows:
Reduced Costs: By identifying security issues early, controls are integrated during development, minimizing the need for post-deployment fixes.
Security-First Culture: Secure SDLC fosters an environment where security is a priority for everyone, driving improvements across the entire organization.
Development Strategy: Establishing security requirements from the start enhances the overall development strategy, ensuring all team members understand and follow the product’s security standards.
Improved Security: Once Secure SDLC practices are in place, the organization’s security posture strengthens, significantly lowering the risk of cyberattacks.
Next, we discuss the automation and tools involved in secure SDLC.
Automation and Tools in Secure SDLC
Automation plays a critical role in embedding security into the Software Development Lifecycle, especially within DevOps and CI/CD pipelines. In fast-paced development environments, security automation ensures that security checks are continuously applied without slowing down the process.
Integrating security into DevOps practices, often referred to as DevSecOps, allows security mechanisms to be automated, making them a natural part of code deployment. This helps identify vulnerabilities early in the cycle, reducing the risk of security flaws reaching production.
Static and dynamic analysis tools are essential for maintaining secure code. Static analysis tools examine the source code before execution to detect security issues, while dynamic analysis tools assess the running application for vulnerabilities. Both types of tools are necessary for comprehensive security coverage, allowing teams to catch different categories of flaws at various stages of development.
Continuous integration of security mechanisms ensures that security checks are performed automatically with every code change. This includes automated testing, vulnerability scanning, and compliance checks. By making security a constant element of the CI/CD pipeline, teams can stay proactive in identifying and resolving security issues, resulting in more secure and resilient software from the start.
Read More: Mapping to NIST Cybersecurity Privacy Framework Controls
Conclusion - Seezo’s Approach To SSDLC
Whether you're selling software to customers or developing it for internal operations, it's essential to safeguard your business by ensuring trust in your software, while maintaining the speed and agility needed to stay competitive. Despite this, many organizations still fall short in integrating security into their secure software development lifecycle (SDLC). A common issue is that development teams often view security as a hindrance, seeing it as something that delays progress by requiring code rewrites and slowing down the release of new features to the market. The key lies in strategically implementing best practices, making security an integrated part of the development process rather than a roadblock.
By giving developers the necessary security requirements before coding begins, Seezo ensures that security is built into the development process from day one.