Dec 6, 2024
In the pre-cloud era, firewalls were commonly used to separate internal and external networks, helping to guard assets against harmful network traffic. However, this method is not well-suited for cloud environments, where many applications require internet access and can't be confined to internal networks.
The growing need to protect web applications from increasing threats led to the introduction of Web Application Firewalls (WAF) in the late 1990s. Initially, WAFs helped by blocking illegal character submissions. Over time, they have evolved to sit "inline" between the application and client, filtering HTTP traffic to prevent malicious requests. This blog focuses on Web Application Firewall (WAF) and its salient features.
Web Application Firewall (WAF) - What Is It?
A Web Application Firewall (WAF) is a security tool that protects web applications by filtering and monitoring HTTP/S traffic between a web application and the internet. It operates at the application layer and is designed to detect and block malicious requests that could exploit application vulnerabilities and common attack vectors such as SQL injection, cross-site scripting (XSS), etc. WAFs work by applying pre-defined security rules or policies, which allow legitimate traffic while blocking potentially harmful activity, thereby safeguarding applications from attacks without requiring changes to the application’s code.
WAFs are commonly used to shield websites from zero-day attacks, malware, OWASP Top 10 threats, and impersonation attempts. In cybersecurity, WAFs play a critical role by detecting and preventing several web application vulnerabilities that traditional network firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) might not effectively manage.
Next, let’s discuss the importance of a WAF.
Importance of a Web Application Firewall (WAF)
A Web Application Firewall (WAF) plays a crucial role in safeguarding internet-facing products and services from data leakage. By monitoring and filtering incoming traffic, a WAF helps prevent sensitive information from being exposed through vulnerabilities like SQL injection or Cross-Site Scripting (XSS) attacks. This is especially important for businesses that manage confidential user data.
Another major benefit of using a WAF is ensuring compliance with industry regulations, such as the Payment Card Industry Data Security Standard (PCI DSS). For organizations handling payment data, adhering to PCI DSS is mandatory, and WAFs assist by securing web applications against threats that could compromise customer information.
Additionally, a WAF provides an essential layer of security for web applications. While traditional firewalls focus on protecting the network perimeter, a WAF is designed to defend applications themselves, offering protection at the application layer. This extra layer is vital, especially for businesses that rely heavily on online platforms, as it mitigates the risk of cyberattacks and improves overall security posture. By integrating a WAF into their security framework, organizations can enhance protection against evolving threats and ensure a safer environment for their web-based products.
WAF vs IPS vs NGFW - Key Differences
An IPS (Intrusion Prevention System), WAF (Web Application Firewall), and NGFW (Next-Generation Firewall) serve distinct roles in security. Here’s a breakdown of each:
IPS - Intrusion Prevention System
An IPS provides broad network security, focusing on signature and policy-based detection. It monitors for known vulnerabilities and attack patterns by referencing a signature database and established policies. When traffic deviates from these norms, the IPS raises alerts. Over time, it updates its signatures as new threats emerge. Typically, an IPS protects traffic across protocols like DNS, SMTP, TELNET, RDP, SSH, and FTP, focusing mainly on the network and session layers (layers 3 and 4), with some systems offering limited application layer (layer 7) protection.
WAF - Web Application Firewall
A WAF secures the application layer by analyzing each HTTP/S request in detail. It understands user sessions and application context, acting as a gateway between users and web applications by filtering communications before they reach the app. WAFs allow only permitted actions based on predefined security policies, making them a critical first line of defense against the OWASP Top 10—a list of the most common application vulnerabilities. Organizations rely on WAFs to safeguard their web applications from targeted attacks.
NGFW - Next-Generation Firewall
An NGFW protects users by monitoring outbound traffic across websites, emails, and SaaS applications, enforcing user-based policies with added context. Unlike a WAF, which typically acts as a reverse proxy for servers, NGFWs often function as forward proxies for clients, such as browsers. NGFWs provide additional security features like URL filtering, anti-virus/anti-malware, and sometimes built-in IPS capabilities, focusing on enhancing user protection across internet interactions.
What is the Difference Between Blocklist and Allowlist WAFs?
The primary difference between blocklist and allowlist Web Application Firewalls (WAFs) lies in how they filter web traffic to determine what is safe or harmful. Here’s a closer look:
Blocklist WAFs
Definition: A blocklist WAF uses a negative security approach, allowing most traffic to pass through while blocking known threats. It identifies and restricts access to malicious entities based on pre-set threat signatures or patterns.
Functionality: Similar to a bouncer at a club, it denies access only to those flagged as malicious. The blocklist is regularly updated with new threat signatures, including malware and attack-associated IP addresses, to protect against recognized risks.
Management: While relatively easy to implement initially, blocklist WAFs require ongoing updates to stay effective against new threats. They need regular maintenance to adapt to emerging attack methods.
Allowlist WAFs
Definition: Operating on a positive security model, an allowlist WAF only permits pre-approved traffic, blocking everything else by default. This model is like an exclusive event where only invited guests are granted access.
Functionality: It defines acceptable, safe inputs and rejects any requests that don’t match these criteria. This approach is more secure, limiting exposure to unknown threats by allowing only trusted traffic.
Management: Setting up an allowlist can be more complex, as it requires a thorough understanding of legitimate traffic patterns, but it leads to fewer false positives and stronger protection against zero-day vulnerabilities.
Read More: What is Web Application Security: Threats & Best Practices
Next, we discuss the working of a WAF.
Web Application Firewall (WAF) - How Does It Work?
Web Application Firewall (WAF) acts as a reverse proxy, positioned between the client and the web application server to protect against malicious activity. It functions at Layer 7 (the application layer) of the OSI model, ensuring that clients communicate only with the WAF rather than directly with the backend system. This setup remains transparent to users, maintaining a seamless experience.
The WAF inspects all incoming client requests and outgoing server responses, allowing it to detect and block traffic that breaches security policies. The WAF's role as a security layer is shown in the architecture, where it integrates smoothly into the communication flow between clients and the server.
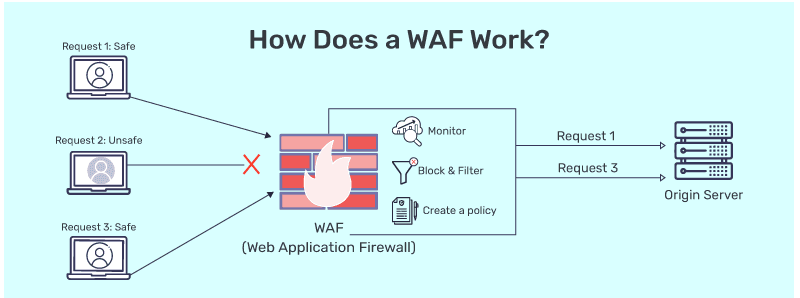
To filter traffic, WAFs employ various strategies:
Positive Security Model: This model allows only known, legitimate traffic by explicitly defining acceptable behaviors and patterns, enhancing protection through a whitelist approach.
Negative Security Model: This model identifies and blocks traffic based on known malicious patterns or signatures, rejecting anything that matches predefined attack patterns, thus working as a blacklist.
Advanced Features: Machine learning and threat intelligence are utilized to defend proactively against advanced threats.
While many WAFs require regular policy updates to address emerging vulnerabilities, machine learning has introduced automatic updates, an essential feature given the rapidly evolving threat environment. WAFs can be deployed as software, appliances, or as-a-service, offering customizable policies to suit the specific needs of web applications.
Next, we discuss the types of WAF deployment.
Types of WAF Deployment
Web Application Firewalls (WAFs) are crucial for protecting web applications from various security threats. They can be deployed in three primary ways, each with distinct advantages and considerations.
1. Network-based WAFs
These are typically hardware-based solutions installed locally within an organization's network. By being physically close to the application, network-based WAFs significantly reduce latency, enhancing performance. However, they are often the most expensive option due to high upfront capital expenditures and ongoing maintenance costs associated with physical hardware management. This type of WAF is ideal for organizations that prioritize speed and have the resources to manage complex hardware setups.
2. Host-based WAFs
Integrated directly into the application code, host-based WAFs offer cost-effective solutions in comparison to their network-based counterparts. They allow for greater customization since they can be tailored specifically to the application's needs. However, this deployment type can consume local server resources and may complicate administration and maintenance tasks. Host-based WAFs are suitable for organizations looking for flexibility without the high costs associated with hardware solutions.
3. Cloud-based WAFs
Cloud-based WAFs provide a low-cost and easily deployable option, often requiring minimal setup beyond a simple DNS change. They operate on a subscription basis, allowing organizations to avoid hefty upfront investments while benefiting from continuous updates and real-time threat intelligence from third-party providers. This deployment model is particularly advantageous for businesses that require scalability and quick implementation without the burden of managing physical infrastructure.
In summary, the choice of WAF deployment—network-based, host-based, or cloud-based—depends on an organization's specific needs regarding cost, performance, and resource management. Each type of WAF offers unique benefits that cater to different operational requirements.
What are the Different Ways To Deploy a WAF?
A WAF can be deployed in various ways depending on factors such as where your applications are hosted, the services you need, your management preferences, and the desired balance between flexibility and performance. Consider whether you want to manage the WAF in-house or outsource it, and decide if a cloud-based solution or an on-premises setup is best. Your choice of deployment method will help determine the ideal WAF for your needs. Here are some deployment options:
WAF Deployment Options:
Cloud-based, Fully Managed Service: Ideal for quick, hassle-free deployment with minimal involvement, especially useful for organizations with limited in-house security resources.
Cloud-based, Self-Managed: Offers cloud flexibility and policy portability while allowing you to retain full control over traffic management and security settings.
Cloud-based, Auto-Provisioned: Provides a straightforward, cost-effective way to deploy WAF in the cloud, automating the setup of security policies.
On-premises Advanced WAF (virtual or hardware appliance): Suited for environments with high-performance demands and complex security needs where flexibility and advanced protection are critical.
Read More: Types of Application Security Testing Tools
What are the various advantages and inherent traits of WAF? Let’s discuss it in the next section.
Web Application Firewall (WAF) - Features and Advantages
Web Application Firewalls (WAFs) offer several key features to shield web applications from a wide array of online threats. Here are some notable features and their associated benefits:
Defense Against Attacks: WAFs are crucial in preventing common web threats like SQL injection and Cross-Site Scripting (XSS). By filtering and monitoring HTTP traffic between the application and the internet, WAFs can detect and block harmful requests before they can compromise the application, protecting sensitive information and ensuring the application's integrity.
Monitoring and Logging: WAFs provide robust monitoring and logging functions, giving organizations the ability to track and analyze incoming traffic patterns. This real-time insight is essential for detecting security threats as they occur. Logs can capture details such as the timing of requests, matched rules, and attack patterns, making them valuable for forensic analysis and meeting compliance requirements.
Scalability for High-Traffic Applications: WAFs are built to manage large volumes of traffic, making them ideal for applications with varying user demands. They can be deployed in multiple configurations—whether network-based, host-based, or cloud-based—allowing businesses to adjust their security measures as needed without affecting performance.
Flexible Deployment Options: WAFs can be implemented across different environments, including on-premises, cloud-based, or hybrid infrastructures. This flexibility allows organizations to maintain strong security across various application architectures while optimizing resource usage.
What is the underlying difference between WAF and other security tools? We will discuss it next.
WAFs vs. Other Security Tools
Web Application Firewalls (WAFs) have distinct functionalities compared to other security solutions, but they are not designed to be a comprehensive security tool. WAFs are meant to work alongside other security measures, forming part of a broader, integrated defense system to tackle various types of attacks.
WAFs vs. Traditional Firewalls
Traditional firewalls establish a boundary that separates internal network resources from those interacting with the internet. In contrast, WAFs provide more specialized protection, allowing applications to connect with the internet while safeguarding against specific threats.WAFs vs. Next-Generation Firewalls (NGFWs)
Next-generation firewalls combine features of traditional network firewalls and WAFs. While NGFWs filter incoming requests by inspecting network packets, they also include additional capabilities such as antivirus, antimalware, and user-based policy enforcement. They provide deeper context on network traffic and use threat intelligence to assist in decision-making.
Although WAFs and NGFWs overlap in some functions, the primary difference lies in their focus. WAFs operate solely at the application layer, protecting against specific web-based threats like XSS or DDoS attacks. On the other hand, NGFWs offer a broader scope by securing the network and adding protection for internal clients. WAFs typically function as reverse proxies, while NGFWs act as forward proxies, protecting clients.
WAFs vs. Intrusion Prevention Systems (IPS)
Like WAFs, Intrusion Prevention Systems (IPS) aim to block harmful traffic, but they cover all protocols, not just web-based ones. WAFs tend to excel at identifying and preventing more complex web-based attacks, using contextual data such as traffic history and user behavior to detect malicious activity. In contrast, IPS solutions rely more on predefined attack signatures and lack the same level of application-specific detection.
Read More: Inherent Risk vs Residual Risk - How Are They Different?
Conclusion
As cyberattacks grow more sophisticated, businesses and organizations must be one step ahead of emerging threats to safeguard their data from malicious activities. Back-end databases, which store sensitive information, are vulnerable to exploitation through weaknesses in web applications. Implementing a Web Application Firewall (WAF) can play a vital role in a company's security framework, helping to prevent data breaches and protect against unauthorized access.
However, it is the best approach if you can embed security from the first line of code itself.
Looking to enhance your software’s security from the start? Begin incorporating automated security design reviews with Seezo.io and ensure solid protection from the initial line of code. Schedule a demo today!

